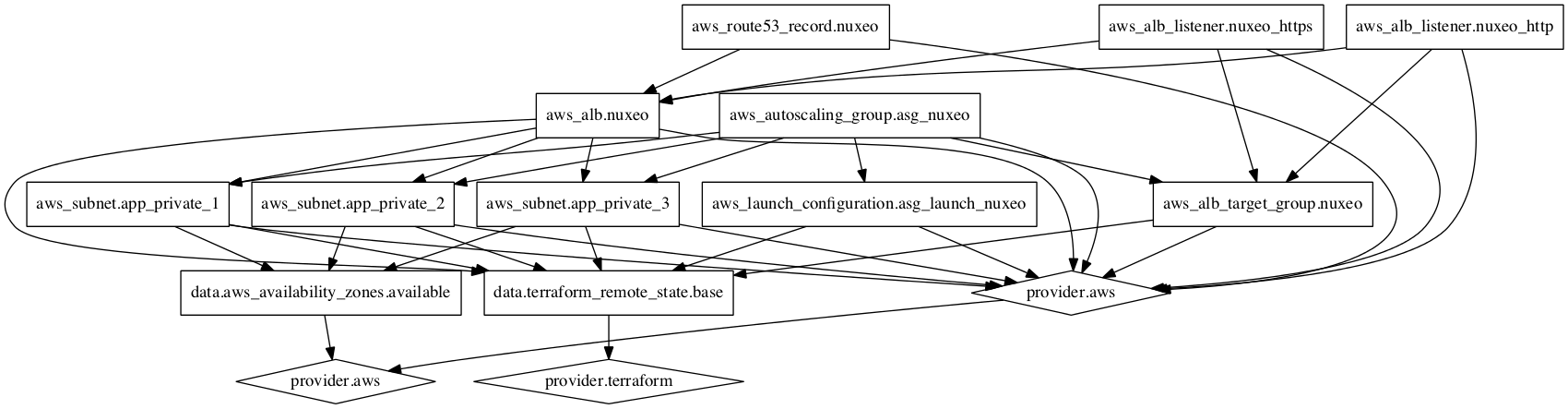
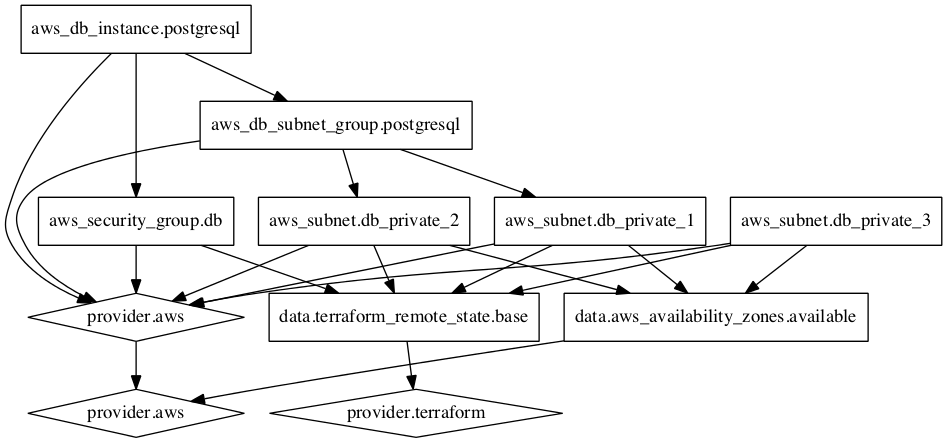
|
|
@@ -1,324 +0,0 @@
|
|
|
-///////////////////////////////////////////////////////////////////////
|
|
|
-// RESOURCES
|
|
|
-///////////////////////////////////////////////////////////////////////
|
|
|
-#-------------
|
|
|
-# DNS Entry for Cloud Customer
|
|
|
-#-------------
|
|
|
-#resource "aws_route53_record" "dns" {
|
|
|
-# zone_id = "Z1EFT3O5K9NMCJ" // Zone ID for nuxeocloud.com
|
|
|
-# name = "${name}"
|
|
|
-# type = "CNAME"
|
|
|
-# ttl = "300"
|
|
|
-# weighted_routing_policy {
|
|
|
-# weight = 90
|
|
|
-# }
|
|
|
-# set_identifier = "${var.stack_name}"
|
|
|
-# records = ["${var.stack_name}.nuxeocloud.com"]
|
|
|
-#}
|
|
|
-
|
|
|
-#-------------
|
|
|
-# CREATE SUBNETS
|
|
|
-#-------------
|
|
|
-resource "aws_subnet" "public" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- cidr_block = "${var.public_subnets[count.index]}"
|
|
|
- availability_zone = "${var.region}${var.azs[count.index]}"
|
|
|
- count = "${length(var.public_subnets)}"
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-subnet-public-${var.region}${element(var.azs, count.index)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-subnet"
|
|
|
- }
|
|
|
- map_public_ip_on_launch = "true"
|
|
|
-}
|
|
|
-
|
|
|
- resource "aws_subnet" "private" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- cidr_block = "${var.private_subnets[count.index]}"
|
|
|
- #availability_zone = "${var.region}${var.azs[count.index]}"
|
|
|
- count = "${length(var.private_subnets)}"
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-subnet-private-${var.region}${element(var.azs, count.index)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-subnet"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-resource "aws_subnet" "db_private" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- cidr_block = "${var.private_db_subnets[count.index]}"
|
|
|
- availability_zone = "${var.region}${var.azs[count.index]}"
|
|
|
- count = "${length(var.private_db_subnets)}"
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-db-subnet-private-${var.region}${element(var.azs, count.index)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-subnet"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-#-------------
|
|
|
-# CREATE NAT GATEWAY
|
|
|
-#-------------
|
|
|
-# > Create EIP to associate to NAT GW
|
|
|
-resource "aws_eip" "nateip" {
|
|
|
- vpc = true
|
|
|
- count = "${length(var.private_subnets) * lookup(map(var.enable_nat_gateway, 1), "true", 0)}"
|
|
|
- tags {
|
|
|
- Name = "${var.vpc_id}-nat-eip"
|
|
|
- billing-category = "customers"
|
|
|
- role = "nuxeo.aws-nat_eip"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-# > Create NAT GW
|
|
|
-resource "aws_nat_gateway" "natgw" {
|
|
|
- allocation_id = "${element(aws_eip.nateip.*.id, count.index)}"
|
|
|
- subnet_id = "${element(aws_subnet.public.*.id, count.index)}"
|
|
|
- count = "${length(var.private_subnets) * lookup(map(var.enable_nat_gateway, 1), "true", 0)}"
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-natgw"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-natgw"
|
|
|
- }
|
|
|
- depends_on = ["aws_internet_gateway.igw"]
|
|
|
-}
|
|
|
-
|
|
|
-# > Create IGW
|
|
|
-resource "aws_internet_gateway" "igw" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
-}
|
|
|
-
|
|
|
-#-------------
|
|
|
-# CREATE ROUTES
|
|
|
-#-------------
|
|
|
-
|
|
|
-# > Route Tables
|
|
|
-
|
|
|
-# >> Route Table for Public Subnets
|
|
|
-resource "aws_route_table" "public" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- propagating_vgws = ["${var.public_propagating_vgws}"]
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-rt-public"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-rtb"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-# >> Route Table for Private Subnets
|
|
|
-resource "aws_route_table" "private" {
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- propagating_vgws = ["${var.private_propagating_vgws}"]
|
|
|
- count = "${length(var.private_subnets)}"
|
|
|
- tags {
|
|
|
- Name = "${var.stack_name}-rt-private-${element(var.azs, count.index)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-rtb"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-# > Associations
|
|
|
-# >> for Private Subnets
|
|
|
-resource "aws_route_table_association" "private" {
|
|
|
- count = "${length(var.private_subnets)}"
|
|
|
- subnet_id = "${element(aws_subnet.private.*.id, count.index)}"
|
|
|
- route_table_id = "${element(aws_route_table.private.*.id, count.index)}"
|
|
|
-}
|
|
|
-
|
|
|
-# >> for Public Subnets
|
|
|
-resource "aws_route_table_association" "public" {
|
|
|
- count = "${length(var.public_subnets)}"
|
|
|
- subnet_id = "${element(aws_subnet.public.*.id, count.index)}"
|
|
|
- route_table_id = "${aws_route_table.public.id}"
|
|
|
-}
|
|
|
-
|
|
|
-# > Routes
|
|
|
-# >> Route for IGW
|
|
|
-resource "aws_route" "public_internet_gateway" {
|
|
|
- route_table_id = "${aws_route_table.public.id}"
|
|
|
- destination_cidr_block = "0.0.0.0/0"
|
|
|
- gateway_id = "${aws_internet_gateway.igw.id}"
|
|
|
-}
|
|
|
-
|
|
|
-# Route for NAT GW
|
|
|
-resource "aws_route" "private_nat_gateway" {
|
|
|
- route_table_id = "${element(aws_route_table.private.*.id, count.index)}"
|
|
|
- destination_cidr_block = "0.0.0.0/0"
|
|
|
- nat_gateway_id = "${element(aws_nat_gateway.natgw.*.id, count.index)}"
|
|
|
- count = "${length(var.private_subnets) * lookup(map(var.enable_nat_gateway, 1), "true", 0)}"
|
|
|
-}
|
|
|
-
|
|
|
-
|
|
|
-#-------------------
|
|
|
-# Security Groups
|
|
|
-#-------------------
|
|
|
-resource "aws_security_group" "sg_external_elb" {
|
|
|
- name = "${format("%s-sg-external-elb", var.stack_name)}"
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- description = "Allows external ELB traffic"
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 80
|
|
|
- to_port = 80
|
|
|
- protocol = "tcp"
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 443
|
|
|
- to_port = 443
|
|
|
- protocol = "tcp"
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- egress {
|
|
|
- from_port = 0
|
|
|
- to_port = 0
|
|
|
- protocol = -1
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- lifecycle {
|
|
|
- create_before_destroy = true
|
|
|
- }
|
|
|
- tags {
|
|
|
- Name = "${format("%s external elb", var.stack_name)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-sg.external"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-resource "aws_security_group" "sg_internal" {
|
|
|
- name = "${format("%s-sg-internal-elb", var.stack_name)}"
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
- description = "Allows external ELB traffic"
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 80
|
|
|
- to_port = 80
|
|
|
- protocol = "tcp"
|
|
|
- security_groups = ["${aws_security_group.sg_external_elb.id}"]
|
|
|
- }
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 8080
|
|
|
- to_port = 8080
|
|
|
- protocol = "tcp"
|
|
|
- security_groups = ["${aws_security_group.sg_external_elb.id}"]
|
|
|
- }
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 22
|
|
|
- to_port = 22
|
|
|
- protocol = "tcp"
|
|
|
- # TOFIX to replace by bastion host
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- egress {
|
|
|
- from_port = 0
|
|
|
- to_port = 0
|
|
|
- protocol = -1
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- lifecycle {
|
|
|
- create_before_destroy = true
|
|
|
- }
|
|
|
- tags {
|
|
|
- Name = "${format("%s internal elb", var.stack_name)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role = "nuxeo.aws-sg.internal"
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-resource "aws_security_group" "external_ssh" {
|
|
|
- name = "${format("%s-sg-external-ssh", var.stack_name)}"
|
|
|
- description = "Allows ssh from the world"
|
|
|
- vpc_id = "${var.vpc_id}"
|
|
|
-
|
|
|
- ingress {
|
|
|
- from_port = 22
|
|
|
- to_port = 22
|
|
|
- protocol = "tcp"
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- egress {
|
|
|
- from_port = 0
|
|
|
- to_port = 0
|
|
|
- protocol = "-1"
|
|
|
- cidr_blocks = ["0.0.0.0/0"]
|
|
|
- }
|
|
|
-
|
|
|
- lifecycle {
|
|
|
- create_before_destroy = true
|
|
|
- }
|
|
|
- tags {
|
|
|
- Name = "${format("%s external ssh", var.stack_name)}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role= "nuxeo.aws-sg-ssh"
|
|
|
- }
|
|
|
- tags {
|
|
|
- }
|
|
|
-}
|
|
|
-
|
|
|
-#-------------------
|
|
|
-# ELB
|
|
|
-#-------------------
|
|
|
-resource "aws_elb" "elb" {
|
|
|
- name = "elb-${var.stack_name}"
|
|
|
-
|
|
|
- internal = true
|
|
|
- cross_zone_load_balancing = true
|
|
|
- subnets = ["${aws_subnet.public.id}"]
|
|
|
- security_groups = ["${aws_security_group.sg_external_elb.id}"]
|
|
|
-
|
|
|
- idle_timeout = 30
|
|
|
- connection_draining = true
|
|
|
- connection_draining_timeout = 15
|
|
|
-
|
|
|
- listener {
|
|
|
- lb_port = 80
|
|
|
- lb_protocol = "http"
|
|
|
- instance_port = 80
|
|
|
- instance_protocol = "http"
|
|
|
- }
|
|
|
-
|
|
|
-# listener {
|
|
|
-# lb_port = 443
|
|
|
-# lb_protocol = "https"
|
|
|
-# instance_port = 80
|
|
|
-# instance_protocol = "http"
|
|
|
-# #ssl_certificate_id = "${var.ssl_certificate_id}"
|
|
|
-# }
|
|
|
-
|
|
|
- health_check {
|
|
|
- healthy_threshold = 2
|
|
|
- unhealthy_threshold = 2
|
|
|
- timeout = 5
|
|
|
- target = "TCP:8080"
|
|
|
- interval = 30
|
|
|
- }
|
|
|
-
|
|
|
-# access_logs {
|
|
|
-# bucket = "${var.log_bucket}"
|
|
|
-# }
|
|
|
- tags {
|
|
|
- Name = "elb-${var.stack_name}"
|
|
|
- billing-category = "customers"
|
|
|
- billing-subcategory = "${var.stack_name}"
|
|
|
- role= "nuxeo.elb"
|
|
|
- }
|
|
|
- tags {
|
|
|
- }
|
|
|
-}
|