+ 0
- 0
examples/alb/graph.png → examples/ha_instance/graph.png
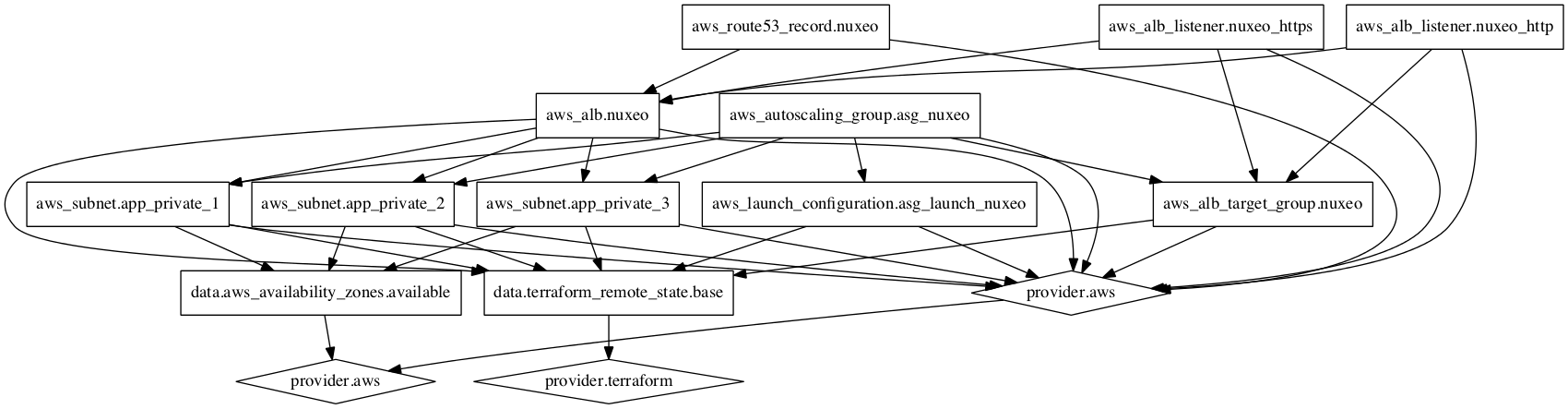
+ 1
- 1
examples/alb/main.tf → examples/ha_instance/main.tf
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 0
examples/alb/outputs.tf → examples/ha_instance/outputs.tf
+ 0
- 0
examples/alb/provider.tf → examples/ha_instance/provider.tf
+ 0
- 0
examples/alb/terraform.tfvars → examples/ha_instance/terraform.tfvars
+ 2
- 0
ha_instance/asg.tf
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 65
- 0
ha_instance/iam.tf
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 0
- 11
s3/s3.tf
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||
+ 1
- 0
vpc/eip.tf
|
||
|
||
|
||
|
||
|
||
+ 1
- 0
vpc/igw.tf
|
||
|
||
|
||
|
||
|
||
+ 1
- 0
vpc/nat.tf
|
||
|
||
|
||
|
||
|
||
+ 0
- 1
vpc/routes.tf
|
||
|
||
|
||
|
||
|
||
|
||
|
||
|
||